Assignment #2
Security in Computing代写 (a): Suppose there are seven voters to vote for YES or NO to give their opinions.Design a secure voting prototype
Security in Computing COSC2536/2537 Total Marks: 35
Submission Deadline: Week 10, May 11 2018 11:59pm
Q1 (Privacy) (Mark 6)Security in Computing代写
Answer either Question (a) or (b)
(a): Suppose there are seven voters to vote for YES or NO to give their opinions.

Design a secure voting prototype as shown in Fig. 1 using Paillier cryptosystem where the votes must be encrypted from Voting Booth before sending them to the Voting Server. Assume, four voters will vote for YES and three voters will vote for NO. The Voting Authority should find four YESs and three NOs after counting the votes. The Voting Authority chooses p=59, q=97 and select g=5724. Seven voters select the random numbers as r1=90,r2=91,r3=92,r3=93,r5=94,r6=95andr7=96,espectively. Show the encryption, homomorphic computations and decryption processes.
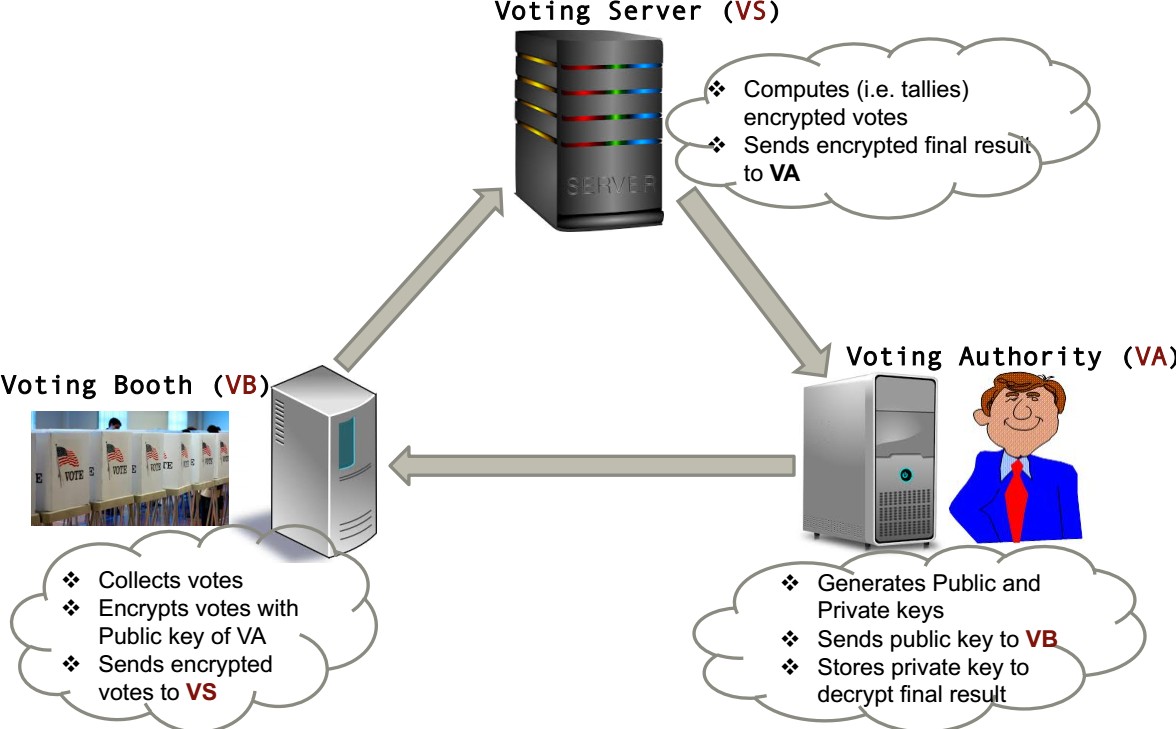
Fig. 1: Secure E-voting Scenario
Hints: Refer to the lecture-5 Secure e voting. You need to represent the total number of votes by 6-bit string. The first three of bits should represent the votes for YES and the rest for NO. When adding a vote for YES, the system adds 001000, which is 8 in integer. Similarly, the system adds 000001 when voting for NO, which is 1 in the integer form.Security in Computing代写
(b)As shown in Fig. 2,
Alice owns two different shops where she sells mobile phones ofa specific The prices of the phones are different based on the shops. Now with
the help of a third-party cloud server, Alice wants to know remotely and securely, how much she earned by selling the mobile phones in both shops with different price rate (assume that Alice does not have the homomorphic computation power). Note that, Alice does not want to reveal how many phones are sold also the total amount of money that she earned to the server.Security in Computing代写
How can you build a secure protocol using Exponential ElGamal cryptosystem where the cloud server can perform such computations without knowing the number of phones that are sold and the total earnings?
Please refer to the below table for detail information.
| Shops | Shop 1 | Shop 2 |
| Phones sold | 20 | 25 |
| Price rate | 50Security in Computing代写 | 30 |
| Total Earning per shop | 1000 | 750 |
| Total Earning | 1750 | |
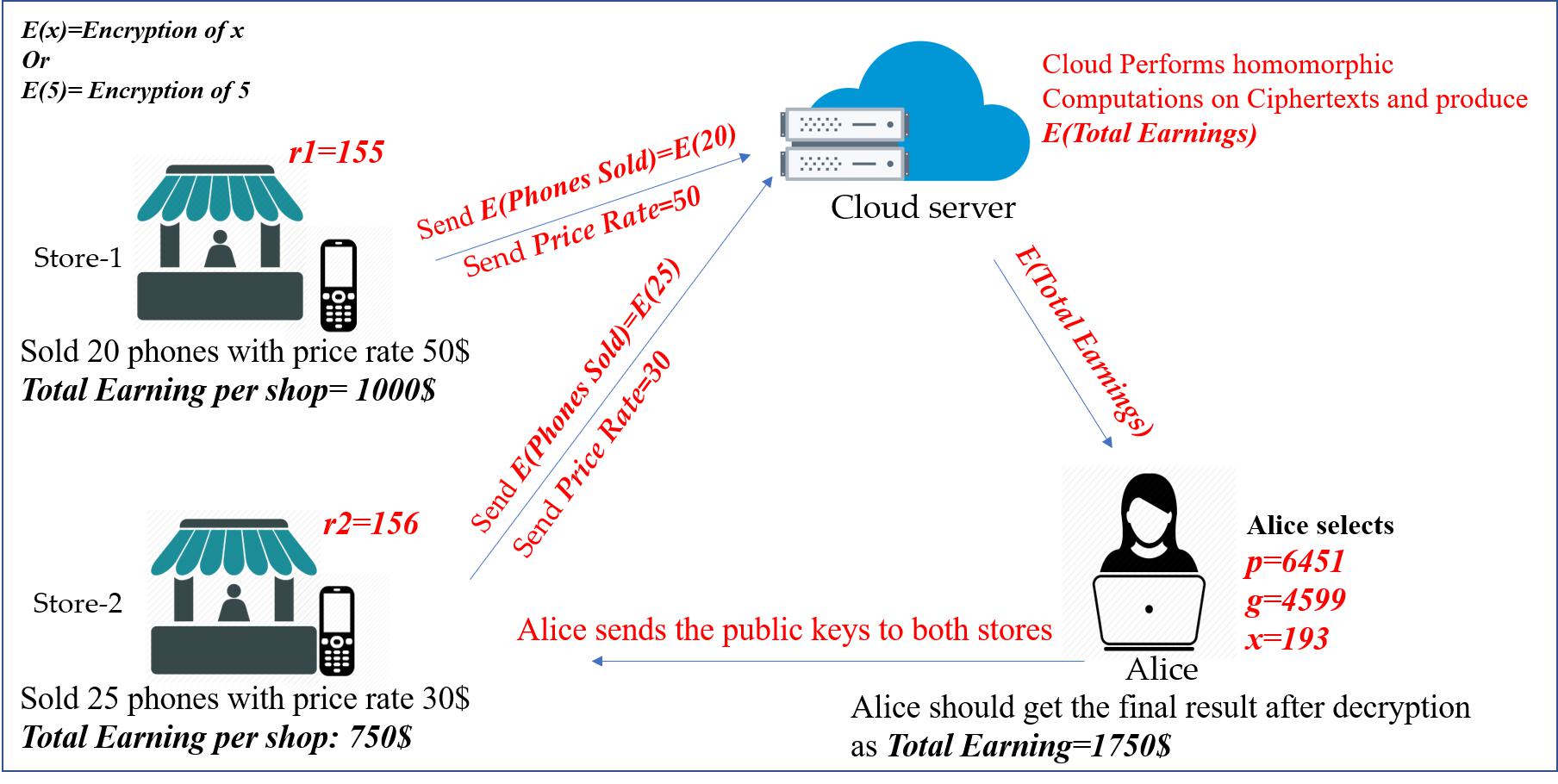
Fig. 2: Secure Transactions
Hints: Alice as a receiver, should generate the public and private key pairs (as shown in figure) and sends the public keys to the shops. The corresponding shops as senders can encrypt (with random numbers given in the figure) the number of phones sold and send the cipher-texts with the price rate (as plaintext) to the cloud server. The server with computation power should perform the required computations homomorphically so that it cannot reveal the total amount that is earned by selling the phones, since it is privacy sensitive. Only Alice should decrypt and find the Total earning.Security in Computing代写

Q2 (Signatures) (Mark 2+2+1+1=6)Security in Computing代写
(a)
Suppose Bob (the sender) wants to send a signed message m=456789 to Alice (the receiver). However, before sending the message he would like to sign the message. When Alice receives the signed message, she would like to verify that the message is
indeed from Bob. To facilitate signing and verification Bob generates public and private keys using RSA encryption algorithm and sends the public key to Alice. Bob uses parameter p=10009 and q=9739, and chooses a suitable public key parameter e=5737. How would Bob sign message m=456789? How would Alice verify the signed message from Bob?Security in Computing代写
(b)Security in Computing代写
Suppose Bob (the sender) wants to send a signed message m=3456 to Alice (the receiver). However, before sending the message he would like to sign the message. When Alice receives the signed message, she would like to verify that the message is indeed from Bob. To facilitate signing and verification Bob generates public and private keys using ElGamal encryption algorithm and sends the public key to Alice. Bob chooses p=8081, g=2849, x=59. How would Bob sign message m=3456? How would Alice verify the signed message from Bob?
(c)
Recall that we use both a public key system and a hash function when computing digital signatures. Suppose that the hash function used to compute and verify signatures is insecure, but the public key system is secure. Show that you can forge signatures.Security in Computing代写
(d)
Why is it a bad idea to use the same RSA key pair for both signing and decryption? Explain with an example (i.e. a numerical example). Is this also true for ElGamal?
Q3 (BlockChain) (Mark 12)
Study (i.e. research) various supply-chain systems as listed below. Choose one of the supply-chain systems as a case study (or you may choose any, which is not listed) and write a short report/proposal on how integrity and traceability of the chosen system can be improved by using BlockChain principle. Use plenty of diagrams to explain your concept. We are not asking you to write code and develop the system, but your report should contain enough information for a system architect to understand and build the proposed system. Some existing Blockchain based Supply-chain case studies are as follows.Security in Computing代写
- Blockchain in Pharmaceutical supply chain to prevent counterfeit drugs supply.
- Blockchain based Portlogistics
- Food safety and traceability using Blockchain: Meat traceability, Seafood traceability
- Blockchain based garment products supply
- Tracking and tracing the provenance of diamonds using Security in Computing代写
Some resources to study about existing Blockchain based Supply chain systems to improve the trust, traceability and integrity:
Seafood Traceability using Blockchain
IBM’s Solution on Blockchain based Food Supply chain
Q4 (Authentication and Intrusion Detection) (Mark 2+2+3+2=9)
(a)Security in Computing代写
Consider the following mutual authentication protocol, where KAB is a shared symmetric key. Give two different attacks that Trudy can use to convince Bob that she is Alice.
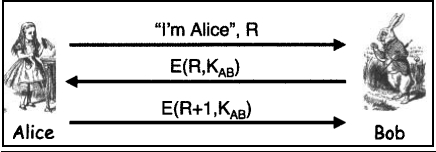
(b)
Suppose R is a random challenge sent in the clear from Alice to Bob and K is a symmetric key known only to Alice and Bob. Which of the following are secure session keys and which are not? Justify your answers.Security in Computing代写
(i)
![]()
(ii)
![]()
(c)
The popular method for anomaly-based intrusion detection is based on file-use statistics.Security in Computing代写
(i)Many other statistics could be used as part of an anomaly-based IDS. For example, network usage would be a sensible statistic to consider. List five other statistics that could reasonably be used in an anomaly-based IDS.
(ii)Whymight it be a good idea to combine several statistics rather than relying on just a few?
(iii)Why might it not be a good idea to combine several statistics rather than relying on just afew?Security in Computing代写
(d)
Alice forgets her password. She goes to the system administrator’s office, and the admin resets her password and gives Alice the new password.
(i)Why does the SA reset the password instead of giving Alice her previous (forgotten)password? Why should Alice re-reset her password immediately after the SA has reset it?Security in Computing代写
(ii)Suppose that after the SA resets Alice’s password, she remembers her previous password. Alice likes her old password, so she resets it to its previous value. Would it be possible for the SA to determine that Alice has chosen the same password as before? Why or why not?
Q5 (Data Hiding) (Mark 2)Security in Computing代写
Assume that we have a stego ECG signal with 200 samples in which binary bits of a text message is hidden as secret message. There are 168 bits of the binary secret message. A bit is hidden in the least significant bit (LSB) of an ECG sample. Please note that the bits are embedded sequentially. For example, we have a text message “hello world”. The equivalent binary of secret message is:
011010000110010101101100011011000110111100100000011101110110111
1011100100110110001100100
Now, if we hide first 5 bits of the binary string given above in LSB of first 5 ECG samples then the resultant ECG samples will look like as follows:
| ECG
Samples |
Equivalent Binary | Binary After Hiding a bit in LSB
Security in Computing代写 |
| -0.045 | 10111101001110000101000111101100 | 10111101001110000101000111101100 |
| -0.055 | 10111101011000010100011110101110 | 10111101011000010100011110101111 |
| -0.055 | 10111101011000010100011110101110 | 10111101011000010100011110101111 |
| -0.075 | 10111101100110011001100110011010 | 10111101100110011001100110011010 |
| -0.065 | 10111101100001010001111010111000 | 10111101100001010001111010111001 |
| ⁞ | ⁞ | ⁞ |
You need to perform steganalysis to find out the secret text message from the stego ECG signal. In order to do this, convert each ECG samples into 64 bit binary and read corresponding LSB to store. At the end, convert retrieved bits into text.Security in Computing代写
The contents of stego ECG signal file (stego_ecg.txt) are given in the Appendix.
APPENDIX
Stego_ecg.txt:
-0.16999999999999998
-0.16
-0.17
-0.165
-0.15499999999999997
-0.15999999999999998
-0.17
-0.15
-0.10499999999999998Security in Computing代写
-0.045000000000000005
-0.030000000000000002
0.019999999999999997
0.065
0.12000000000000001
0.05499999999999999
0.01
-0.07999999999999999
-0.16
-0.17
-0.19
-0.21499999999999997Security in Computing代写
-0.21499999999999997
-0.4000000000000001
-0.39000000000000007
0.475
2.07
3.28
2.345
0.22499999999999998
-0.48000000000000004
-0.235
-0.23500000000000001
-0.275
-0.26000000000000006Security in Computing代写
-0.26000000000000006
-0.2800000000000001
-0.265
-0.255
-0.2750000000000001
-0.24
-0.24
-0.23
-0.215
-0.195
-0.19000000000000003Security in Computing代写
-0.16999999999999998
-0.175
-0.13500000000000004
-0.12
-0.08
-0.08
-0.08Security in Computing代写
-0.07
-0.055
-0.05
-0.004999999999999999
-0.015
-0.030000000000000002
-0.04
-0.07000000000000002
-0.08
-0.07999999999999999
-0.135
-0.12000000000000001 Security in Computing代写
-0.135
-0.135
-0.17
-0.16499999999999998
-0.175
-0.16499999999999998
-0.14
-0.14
-0.175
-0.13500000000000004
-0.145
-0.14
-0.13000000000000003Security in Computing代写
-0.13
-0.15499999999999997
-0.14000000000000004
-0.16499999999999998
-0.16
-0.13500000000000004
-0.135
-0.165
-0.15
-0.155
-0.15999999999999998
-0.15999999999999998
-0.15499999999999997
-0.17
-0.14999999999999997Security in Computing代写
-0.14999999999999997
-0.15999999999999998
-0.15499999999999997
-0.13
-0.14999999999999997
-0.12000000000000001
-0.10000000000000002
-0.05499999999999999
-0.03
0.045
0.085
0.11
0.09
0.02
-0.10000000000000002Security in Computing代写
-0.14
-0.18500000000000003
-0.19000000000000003
-0.20000000000000004
-0.18000000000000002
-0.395
-0.34500000000000003
0.5200000000000001
2.0299999999999994
3.1300000000000003
2.1600000000000006
0.1
-0.505
-0.26
-0.24000000000000002Security in Computing代写
-0.26000000000000006
-0.26000000000000006
-0.275
-0.24
-0.235
-0.22499999999999998
-0.255
-0.25000000000000006
-0.24000000000000002
-0.19000000000000003
-0.18
-0.19000000000000003
-0.18
-0.165
-0.15999999999999998
-0.12000000000000001
-0.10000000000000002
-0.09500000000000001
-0.07999999999999999
-0.07000000000000002Security in Computing代写
-0.07999999999999999
-0.039999999999999994
-0.06
-0.04
-0.030000000000000002
-0.035
-0.07000000000000002
-0.07
-0.1
-0.105
-0.14
-0.12000000000000001
-0.14000000000000004
-0.14
-0.165
-0.18000000000000002Security in Computing代写
-0.15
-0.13
-0.175
-0.155
-0.13500000000000004
-0.13
-0.14499999999999996
-0.115
-0.12000000000000001
-0.14000000000000004
-0.15
-0.145
-0.15
-0.16
-0.17
-0.145
-0.165
-0.155
-0.18
-0.18
-0.175
-0.165
-0.19
-0.17Security in Computing代写
-0.175
-0.155
-0.12
-0.06
-0.04Security in Computing代写
0.01
0.06
0.1
0.08
0.06
-0.06
-0.12
-0.185
-0.195
-0.2
-0.195
-0.27
-0.425
更多其他:C++代写 考试助攻 C语言代写 计算机代写 report代写 project代写 物理代写 数学代写 java代写 程序代写 algorithm代写 C++代写 r代写 金融经济统计代写 加拿大代写 北美代写

